 |
Cybertelecom Federal Internet Law & Policy An Educational Project |
CODE

|
CODE |
 |
|
History - Timeline - CyberTelecom Reader - Internet History - - Prelude 1950-66 - - - Paul Baran - - ARPANET 1967-69 - - ARPANET 1970s - - - TCP/IP - - 1980s - - - NSFNET - - 1990s - - - CIX - - DNS - - World Wide Web - - VoIP - - Backbone - - Internet2 - - Reference - AT&T - Telephone - Telegraph - Wireless / Radio - Common Carrier - Mergers - FCC - - Communications Act - - Telecom Act - - Hush a Phone - - Computer Inquiries - - Universal Service |

[W]e have every reason to believe that cyberspace, left to itself, will not fulfill the promise of freedom. Left to itself, cyberspace will become a perfoect tool of control. - Lessig, p. 6
Architecture is a kind of law: it determines what people can and cannot do. - Lessig, p. 59
Out of the utopian-cyberlibertarian era emerged a voice that became a drum major for the cyberprogressive movement. Larry Lessig's book CODE and Other Laws of Cyberspace was published in 1999 and quickly became required reading. [Mayer-Schonberger "In many ways, Lawrence Lessig has become the voice of the cyberlaw community."] [Vest] [Declan] The message of the book, reduced down to a slogan, is "Code is Law."
Lessig's CODE is a reaction against the exceptionalist era. Lessig selects one core tenant of that era, but rejects another. Picking up on the exceptionalist mantra, Lessig affirms Cyberspace as a unique and distinct place in two ways.
First, he posits it as a unique oasis where people (some people) can live out their entire lives. He selects an online subculture of individuals whose total social interactive experience is mediated through computer screens, and defines the whole by this part. Cyberspace is distinct because individuals can live their entire lives there (even if only a select few chose to do so). [Lessig at 74 ("For some this [online virtual community] interaction is the most sustained human contact of their lives.")] Second, Cyberspace is unique because it is constructed entirely of code. It is a uniquely artificial space, built by software that controls the form, shape, and depth of that reality. And the one who controls that code controls that space. [Lessig, p. 60 ("If code is law, then... 'control of code is power.'").]
The second core tenant of the Exceptionalist Era was cyberlibertarianism. The uniqueness of cyberspace and the competitive environment it fostered placed it out of the reach of kings, presidents, law or economics. [Clark] It was a space where the rules of the real world did not apply. For Lessig, yes, cyberspace is a unique space, but no, "obviously" libertarianism was to be rejected. [Lessig, p. 5 ("That cyberspace was a place that governments could not control was an idea that I never quite got."); Lessig, Chpt. 17, What Declan Doesn't Get (responding directly to libertarian journalist Declan).] In order to successfully make this rhetorical maneuver, Lessig had to justify why he accepts exceptionalism but rejects its corollary, cyberlibertarianism. Here, Lessig foretells a dire future, driven by businesses seeking profits who consolidate control of the Internet, and government seeking to reestablish sovereignty, which will lead to a future antithetical to the utopian ideals of the exceptionalist era. [Lessig, p. 6 ("[W]e have every reason to believe that cyberspace, left to itself, will not fulfill the promise of freedom. Left to itself, cyberspace will become a perfect tool of control."); Lessig, p. 131 ("Put your Ayn Rand away). But, compare, David G. Post, What Larry Doesn’t Get: Code, Law, and Liberty in Cyberspace, 52 STAN. L. REV. 1439 (2000); Declan McCullagh, What Larry Didnt Get, Ten Years of CODE, CATO Unbound (May 4, 2009); Declan McCullagh, Lessig Suffers from Bad Code, Wired, October 6, 1999. Compare Werbach p. 2 ("The chaotic nature of the Internet may be troubling for governments, which tend to value stability and certainty.")]. Lessig sounds a progressive alarm that "[u]nless someone like you cares a whole lot, nothing is going to get better. It's not." [Dr. Seuss, The Lorax (Random House 1971)] If the ideals of the exceptionalist era are to be maintained, Lessig argues, action must be taken, and this action includes government intervention. Lessig's alarm becomes a rallying cry of the cyber-progressive movement, breaking it free of the shackles of the "don’t fetter the Internet with government regulation" credo. [47 USC s 230(c)(2)]
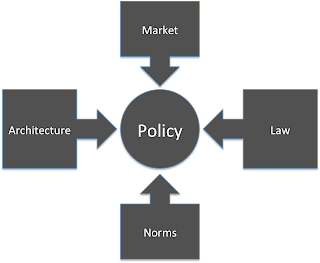
From here, Lessig sets forth a course of action. Lessig presents a methodology of how cyberspace policy should be analyzed pursuant to four modalities: law, norms, economics, and architecture. [Lessig, p. 85.] And here Lessig employs a play on words. Code, of course, is created by legislatures, codified into laws, and determines how we as a society live together (i.e., drive on the right side of the road, able to drive when we are 21, and the right to free speech). CODE, on the other hand, is the architecture of the Internet, created by engineers, which determines how we as a networked community live together (i.e., "@" is a symbol used in email addresses, Twitter messages can only be 160 characters, and once content is released on the Internet, it can be very hard to censor [See, e.g., Kristen Butler, Pirate Bay hosts 3D gun after State Department takedown, UPI May 10, 2013.]). The former is dubbed "East Coast code" and the latter is "West Cost code." [Lessig, p. 53].
Lessig's compelling counsel is the positioning of CODE, or architecture, as a primary modality for analyzing policy. In so doing, Lessig has moved from responding to exceptionalists, to responding to anti-exceptionalists: technophobics as wells as legacy players who, in a knee jerk reaction to change, attempted to reel the Internet back under control by retrofitting outdated laws onto the new medium. Lessig rejects this, arguing that the unique characteristics of the medium must be considered. Cyberspace is a unique virtual reality constructed entirely of CODE. This architecture dictates online that which is and is not permissible. Public policy discussions become defined by the options that the designers of CODE permit. Lessig points to an example of copyright: the Internet was designed to facilitate the free sharing of information, but this collided with copyright interests; a CODE solution of strong DRM might enable perfect control of copyrighted material, but would collide with fair use. [Lessig, p. 122.]
Directly porting laws designed for the legacy world over to the cyberworld is a doomed venture. Instead, the architecture of cyberspace dictates potential policy outcomes. Lessig walks through three policy areas (free speech, privacy, and copyright) demonstrating the application of the four modalities. Annoucing a call to arms, Lessig lays out how things could potentially go horribly wrong, with the Internet transforming from its hippie roots to a monster that monitors and tracks everyone's every move everywhere at any time.
Copyright [p. 122]
Problem: Architecture of the Internet which promotes the free sharing of information and files, resulting in piracy of copyrighted material. eCommerce Solution: Architecture DRM Lessig Problem: But the perfect control of the architecture DRM solution is in conflict with the legal and normative values of fair use, and the rights that copyright consumers have Problem: Few limits on distribution. p. 174. Children's access to pornography. Solution: Architecture: PICS Note: "the values of speech are different from the values of privacy." p. 182. Problem: Architecture enables wide spread electronic surveillance and data gathering. Profiling and the inability to escape or change the profile created by data. "Whereas before there was relative equality because the infromation that enabled discrimination was too costly to acquire, now it pays to discriminate." p. 156 Solution: Law and architecture: Privacy as a property right and use of P3P. "Individuals should be able to control information about themselves." p. 162. "We must build into the architecture a capacity to enable choice - not choice by humans but by machines. The architecture must enable machine-to-machine negotiations about privacy so that individuals can instruct their machines about the privacy they want to protect." p. 163. The architecture of the Internet means that how policy objectives might be achieved in Cyberspace will be markedly different than in the legacy space (and how, if things go sideways and certain interests wrestle control of the architecture, things could go poorly). And while Lessig presents opinions of what the policy outcomes could potentially be, what is more significant is demonstrating what the policy outcomes no longer can be. The architecture of the Internet has changed the dynamic, creating new opportunities and new risks. Whatever the outcome of specific policy discussions (and some of Lessig's comments were met with controversy [Adam Thierer, Code, Pessimism, and the Illusion of "Perfect Control," Ten Years of CODE, CATO Unbound (2009); Marc Rotenberg, Fair Information Practices and the Architecture of Privacy (What Larry Doesn’t Get), 2001 STAN. TECH. L. REV. 1, ¶¶ 80–90 (2001); Schwartz, Paul M., Beyond Lessig's Code for Internet Privacy: Cyberspace Filters, Privacy Control and Fair Information Practices. Wisconsin Law Review, 2000.]), Lessig blasts the discussion out of outdated modes of thinking, placing architecture as the driver.
Lessig's CODE was a persuasive articulation of how Internet policy should be approached. Discussion of architecture became primary to any policy debate. The cyber-progressives pick up on Lessig's message as a rallying cry, arguing that action must be taken to preserve the vibrant nature of the Internet. [Jonathan Zittrain, The Future of the Internet (and how to stop it) (Yale University Press 2009); Timothy Wu, The Master Switch: The Rise and Fall of Information Empires (Vintage 2011).] Lessig's arguments would become influential for the FCC's Open Internet Order, seeking to preserve the original exceptionalist environment of the Internet through FCC intervention. But ultimately the progressives would pursue the mandate that something must be done, while deprecating the first Internet tenant that Lessig adopted. The progressives will begin to argue that something must be done - not because the Internet is a unique - but because the Internet is consistent with the real world, fitting within historical evolution, much in line with Justice Brandeis' calls to revise Fourth Amendment jurisprudence in light of the advances of electronic communications. Something must be done, and the Internet may be wonderous and filled with promise - but gone is the exceptionalist rhetoric of cyberspace as some other space where people live out their entire lives, unreachable by kings or presidents. Instead, it has become a device in our pockets, facilitating our day to day interactions.
Lessig's Four Modalities for analysing technology policy is nothing new. Presented in the Internet era, Lessig's analysis is presented as and was received as novel. But those familar with technology policy know that the architecture of innovation both enables and restrains policy choices. There has been an interplay between technology and law for as long as there has been technology and law. See Timothy Wu, The Master Switch.
At the turn of the century AT&T designed its network to obstruct interconnection with competing networks (railroads did the same thing). This led to Theodore Vail's notion of Universal Service, and the government sanctioned monopoly AT&T. In the mid-century, innovators attemted to connect foreign attachments to the telephone network, which led to AT&T screaming that these foreign attachments harmed the network - when AT&T delineated why their attachments did not harm the network when others did, the FCC codified AT&T's explanation in the Part 68, and the CPE market was born and exploded. In the 1990s, mobile telephone networks where not designed to be compatible with hearing aids, resulting in years of negotiations and regulatory considerations until a solution could be achieved. Lessig merely rearticulates the historical methodology of communications polcy. In a related network, roads, the architecture of the road perhaps is a greater force for legal compliance than the law itself. Roads are designed for different speeds. Highways have long straight aways, and gradual, banked turns, while low speed roads are narrow, crocked, with difficult turns. It is difficult to go 55 mph on a road designed for 25 mph (and that might have speed bumps built into it). Conversely, a road designed for 55 mph, which the local authority seeks to reduce the speed on simply by posting a 35 mph speed limit sign, will generally have difficulty actually achieving the designed behavior by motorists. CODE determining policy options: Others have written on the proposition that architectual determines policy.
Marshall McLuhan, THE GUTENBERG GALAXY 253 (1962) Rohan Samarajiva, Surveillance by Design: Public Networks and the Control of Consumption , in COMMUNICATION BY DESIGN (Robin Mansell & Roger Silverstone eds., 1996) WILLIAM J. MITCHELL , CITY OF BITS : SPACE, PLACE , AND THE I NFOBAHN 112 (1996) The Cyberspace/ Real Space Duality: While moving away from one core belief of the nascent Internet era, cyberlibertarianism, Lessig affirms a different one, that Cyberspace is a unique space distinct from the physical reality through which humans navigate their daily lives. [Lessig, p. 190 "Cyberspace is a place. People live there."] Cyberspace is other; a virtual space constructed entirely of code [p. 71] subject to a new culture and new norms. Lessig maintains the duality between cyberspace and real space, but he does this with a "tail wags the dog" argument. Lessig defines cyberspace by a select subculture of the early Internet community who managed to define a new online social reality devoid of direct human contact. The space of MUDs, where a subculture of individuals devoted enormous time and energy where interactivity was mediated through a computer network - became, to Lessig, the defining culture of the Internet (this is a bit like defining the real world by those who play Dungeons & Dragons).
Of course, this is a neat rhetorical trick: if the reader is convinced that the space is other, than it is easier to convince the reader that the governance should be other. The argument that the governance of cyberspace is unique presumes that cyberspace itself is a unique space (as opposed to a historical evolution described by Justice Brandeis, applying the Fourth Amendment to the new, revolutionary telephone network). Historical evolution, an opposing vision, suggests that there are first principals (constitutional and democratic values), there are evolving historical facts that present new challenges, and there is implementation - where implementation of first principals must change as facts evolve.
There is no basis for defining a whole by a part. There were certainly many, even at that time, that did not view cyberspace as a separate reality, but merely a new communications medium within the one reality that exists. See Licklider, Taylor. The Internet has gone mainstream; for many the Internet has become the device that they have in their pocket that helps them coordinate an engagement, select the best place where they will meet, find directions, check the weather, take pictures, track their fitness performance, and create posts - cyberspace and the real world are indistinguishable. See John Palfrey, Born Digital. There exists no duality and no separation. Cyberspace as a separate space has lost its meaning (if it ever actually had meaning).
Lessig's Distopian Predictions did not pan out. [Theirer] [Declan "Lessig’s predictions of private sector abuses proved to be a bit wide of the mark."]
The book is filled with irrelevant or hypothetical tangents:
"Lessig doesn't offer much proof that a Soviet-style loss of privacy and freedom is on its way. For instance, the book opens with four cyber-horror stories, each of which illustrates ''a theme that recurs throughout the book'': ...But three of the stories are hypothetical (including a silly one involving made-up characters in an online computer game). Where are the real-world examples? Lessig hints that ''architectures of control are possible; they could be added to the Internet that we know.'' Well, of course they could be, but will they be?"- David Pogue, Dont Just Chat, Do Something, New York Times Jan. 30, 2000 "Lessig adds an additional layer of differentiation by talking about East Coast and West Coast Code (East Coast Code referring to Washington, D.C.-imposed statutes, West Coast Code referring to Silicon Valley created software (and, occasionally, hardware)). This may have sounded like a fun idea to Lessig (and it probably goes over well in the classroom), but it is really just pointless obfuscation. " [The Complete Review: CODE] Privacy as Property Lessig's proposal to treat privacy as property received a strong critique from privacy scholars. Marc Rotenberg, Fair Information Practices and the Architecture of Privacy (What Larry Doesn’t Get), 2001 STAN. TECH. L. REV. 1, ¶¶ 80–90 (2001); Schwartz, Paul M., Beyond Lessig's Code for Internet Privacy: Cyberspace Filters, Privacy Control and Fair Information Practices. Wisconsin Law Review, 2000.
Lessig's Solutions Relies Excessively on
Markets [Mayer-Schonberger] Insufficient relying on the market. [Post ("Code is, in short, a dense and multi-layered indictment of the invisible hand. ")] [Declan] [Thierer] Washington Bureaucrats. [Declan] Technodeterminism [Post] The Law (collective action) [Post]
.
CODE has been followed up by other Distopian Cyber Future books such as
Larry Lessig, CODE 2.0 2006 Jonathan Zittrain, The Future of the Internet (and how to stop it), 2009 Timothy Wu, The Master Switch, 2011 Jonathan Zittrain, The Generative Internet , 119 H ARV . L. R EV . 1974 (2006) See Cybertelecom Reader.
codecode